Understanding Blockchain Technology
Published November 2024

Blockchain technology has revolutionized the way we think about data storage, security, and digital transactions. At its core, blockchain is a distributed ledger technology that enables secure, transparent, and tamper-proof record-keeping without the need for a central authority.
What is Blockchain?
A blockchain is essentially a chain of blocks, where each block contains a collection of transactions or data. These blocks are cryptographically linked together, creating an immutable record that cannot be altered without detection. This fundamental structure provides the foundation for cryptocurrencies and numerous other applications.
The term "blockchain" comes from its structure: blocks of data chained together through cryptographic hashes, creating a permanent and verifiable record of all transactions.
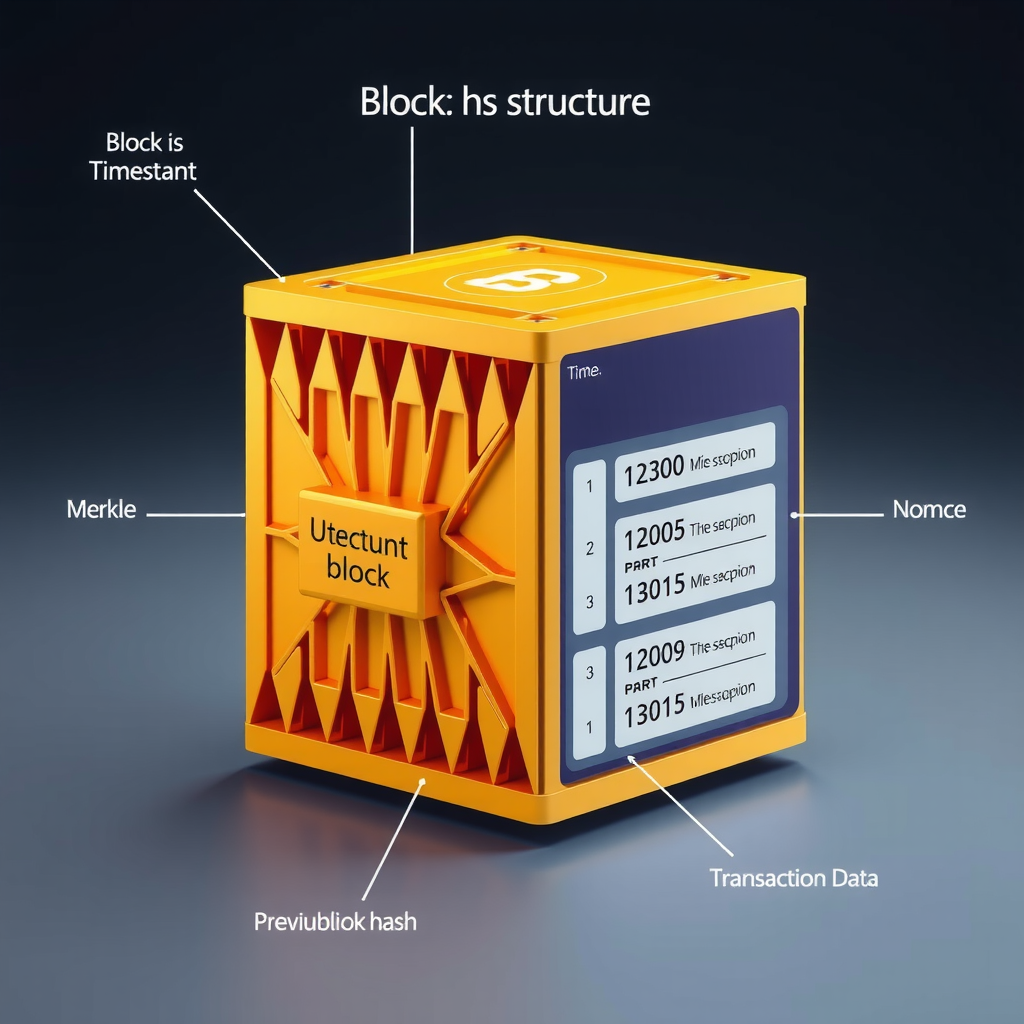
Distributed Ledger Technology
Unlike traditional databases controlled by a single entity, blockchain operates as a distributed ledger. This means that multiple copies of the entire blockchain exist across a network of computers, called nodes. Each node maintains an identical copy of the ledger, ensuring redundancy and eliminating single points of failure.
Traditional Database
- Centralized control
- Single point of failure
- Requires trust in authority
- Vulnerable to manipulation
- Limited transparency
Blockchain Ledger
- Decentralized network
- Highly resilient
- Trustless verification
- Immutable records
- Complete transparency
The distributed nature of blockchain technology provides several key advantages. When a new transaction occurs, it must be validated by multiple nodes in the network before being added to the blockchain. This consensus mechanism ensures that no single entity can manipulate the data without the agreement of the majority of the network.
Consensus Mechanisms
Consensus mechanisms are the protocols that allow all nodes in a blockchain network to agree on the current state of the ledger. Different blockchain platforms utilize various consensus mechanisms, each with its own advantages and trade-offs.
Proof of Work (PoW)
Proof of Work is the original consensus mechanism used by Bitcoin. In PoW, miners compete to solve complex mathematical puzzles. The first miner to solve the puzzle gets to add the next block to the chain and receives a reward. This process, known as mining, requires significant computational power and energy consumption.
Key Features:High security, energy-intensive, slower transaction speeds, proven track record
Proof of Stake (PoS)
Proof of Stake selects validators based on the amount of cryptocurrency they hold and are willing to "stake" as collateral. Validators are chosen to create new blocks based on their stake size and other factors. This mechanism is more energy-efficient than PoW and is used by platforms like the Marinade protocol on Solana.
Key Features:Energy-efficient, faster transactions, requires less hardware, growing adoption
Other Consensus Mechanisms
Beyond PoW and PoS, several other consensus mechanisms have emerged:
- Delegated Proof of Stake (DPoS):Token holders vote for a limited number of delegates who validate transactions
- Proof of Authority (PoA):Validators are pre-approved and identified, suitable for private blockchains
- Proof of History (PoH):Used by Solana, creates a historical record proving events occurred at specific moments
- Byzantine Fault Tolerance (BFT):Ensures consensus even when some nodes fail or act maliciously
Nodes and Network Participants
Nodes are the backbone of any blockchain network. These are individual computers that maintain copies of the blockchain and participate in the validation process. Understanding the different types of nodes helps clarify how blockchain networks function.
Full Nodes
Store the complete blockchain history and validate all transactions and blocks according to consensus rules. Essential for network security and decentralization.
Light Nodes
Store only block headers and request transaction data from full nodes when needed. Require less storage and computational resources, ideal for mobile devices.
Mining/Validator Nodes
Specialized nodes that create new blocks and add them to the blockchain. In PoW systems they're miners; in PoS systems like Marinade Solana, they're validators.
The more nodes a blockchain network has, the more decentralized and secure it becomes. Each node independently verifies transactions, making it extremely difficult for malicious actors to compromise the network. This distributed validation process is what makes blockchain technology so robust and trustworthy.
Mining and Validation Processes
The process of adding new blocks to the blockchain varies depending on the consensus mechanism, but the fundamental goal remains the same: to validate transactions and maintain the integrity of the ledger.
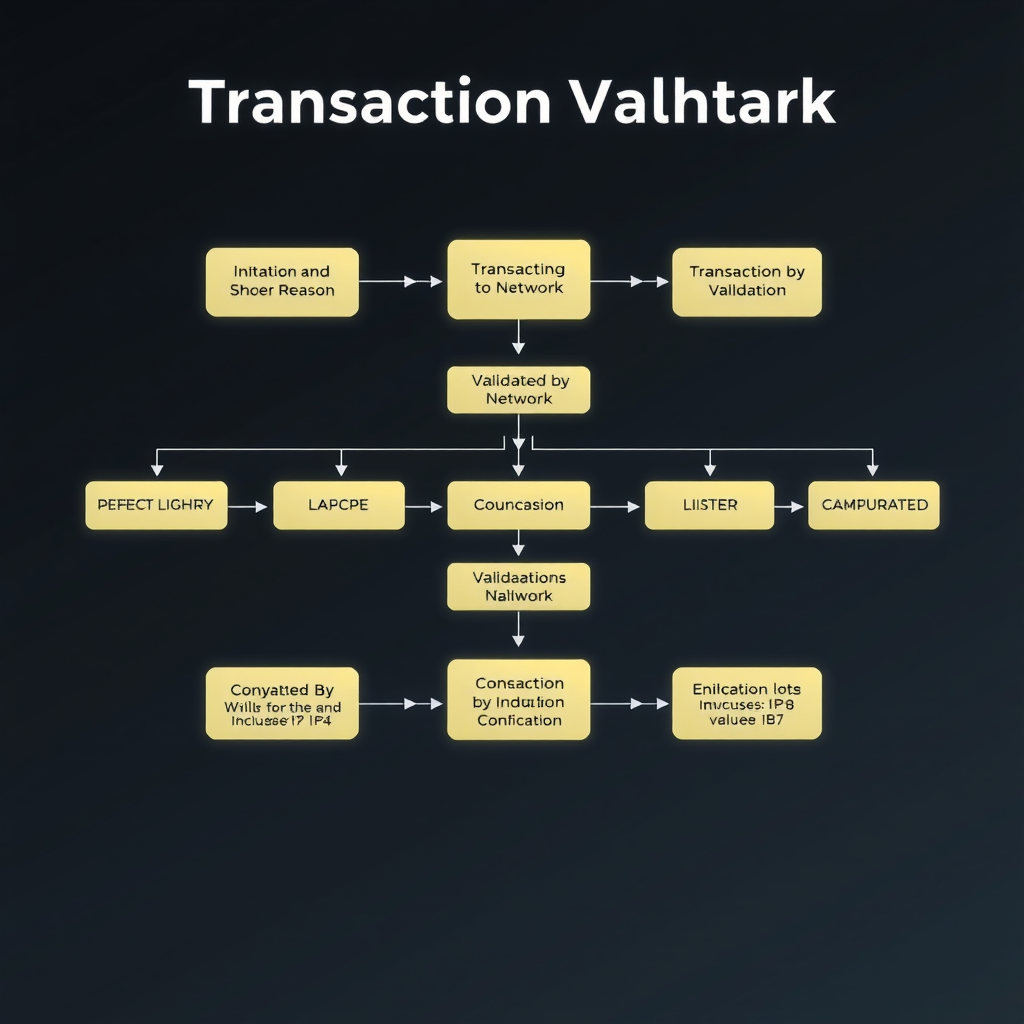
Transaction Validation Steps
- Transaction Initiation:A user creates a transaction and signs it with their private key
- Broadcasting:The transaction is broadcast to the network and enters the mempool (memory pool)
- Verification:Nodes verify the transaction's validity, checking signatures and ensuring sufficient funds
- Block Creation:Miners or validators select transactions from the mempool to include in a new block
- Consensus:The network reaches consensus on the validity of the new block
- Confirmation:The block is added to the blockchain, and the transaction is considered confirmed
In Proof of Work systems, miners compete to solve cryptographic puzzles. The difficulty of these puzzles adjusts automatically to maintain a consistent block creation rate. In Proof of Stake systems like those used by the Marinade platform, validators are selected based on their stake, and they validate transactions without the energy-intensive mining process.
Important:The validation process ensures that double-spending is prevented and that all transactions follow the network's rules. This is achieved without requiring trust in any central authority.
Public vs. Private Blockchains
Blockchains can be categorized into different types based on their accessibility and governance structure. Understanding these differences is crucial for recognizing the appropriate use cases for each type.
Public Blockchains
Public blockchains are open to anyone. Anyone can join the network, participate in the consensus process, and view all transactions. Examples include Bitcoin, Ethereum, and Solana.
Advantages:
- Complete transparency
- Maximum decentralization
- Censorship resistance
- No single point of control
Challenges:
- Slower transaction speeds
- Higher energy consumption (PoW)
- Scalability limitations
- Less privacy
Private Blockchains
Private blockchains restrict access to authorized participants only. They are typically used by enterprises and organizations for internal processes and supply chain management.
Advantages:
- Faster transaction speeds
- Greater privacy control
- Lower operational costs
- Easier governance
Challenges:
- Less decentralized
- Requires trust in administrators
- Limited transparency
- Potential for censorship
Hybrid and Consortium Blockchains
Between public and private blockchains exist hybrid models that combine elements of both. Consortium blockchains are controlled by a group of organizations rather than a single entity, offering a middle ground between full decentralization and centralized control.
These models are particularly useful for industries where multiple organizations need to collaborate while maintaining some level of control and privacy, such as in banking consortiums or supply chain networks.
How Cryptocurrencies Utilize Blockchain
Cryptocurrencies are the most well-known application of blockchain technology. They leverage blockchain's core features to create digital currencies that operate without central banks or governments.
Key Blockchain Features for Cryptocurrencies
Immutability
Once a transaction is recorded on the blockchain, it cannot be altered or deleted. This prevents fraud and ensures the integrity of the transaction history. Each block contains a cryptographic hash of the previous block, creating an unbreakable chain.
Transparency
All transactions on public blockchains are visible to anyone. While wallet addresses are pseudonymous, the transaction history is completely transparent. This transparency builds trust and allows for public auditing of the entire system.
Security
Blockchain uses advanced cryptography to secure transactions. Each user has a pair of cryptographic keys: a public key (like an account number) and a private key (like a password). Transactions are signed with private keys, ensuring that only the owner can authorize transfers.
Decentralization
No single entity controls the cryptocurrency network. This eliminates the need for intermediaries like banks and reduces the risk of censorship or manipulation. Projects like the Marinade protocol exemplify this decentralized approach on the Solana blockchain.
Different cryptocurrencies implement blockchain technology in various ways. Bitcoin focuses on being a digital currency and store of value. Ethereum extends blockchain functionality with smart contracts, enabling programmable transactions. Solana emphasizes high-speed transactions and scalability, making it suitable for decentralized applications and platforms like Marinade technology.
Practical Examples and Use Cases
Understanding blockchain becomes clearer when examining real-world applications. Beyond cryptocurrencies, blockchain technology is being adopted across various industries.
Supply Chain Management
Companies use blockchain to track products from manufacture to delivery. Each step in the supply chain is recorded on the blockchain, providing complete transparency and preventing counterfeiting.
Example: Tracking organic food products from farm to table, ensuring authenticity and quality.
Digital Identity
Blockchain enables secure, self-sovereign digital identities. Users control their own identity data and can selectively share information without relying on centralized authorities.
Example: Verifying credentials and certifications without contacting issuing institutions.
Smart Contracts
Self-executing contracts with terms directly written into code. They automatically execute when predetermined conditions are met, eliminating the need for intermediaries.
Example: Automated insurance payouts when flight delays are confirmed by oracle data.
Decentralized Finance (DeFi)
Financial services built on blockchain that operate without traditional intermediaries. Users can lend, borrow, trade, and earn interest on their crypto assets.
Example: The Marinade project on Solana enables liquid staking, allowing users to stake SOL while maintaining liquidity.
Understanding Blockchain Security
Blockchain's security model is fundamentally different from traditional systems. Understanding how blockchain achieves security helps explain why it's considered one of the most secure technologies available.
Cryptographic Hashing
Each block contains a cryptographic hash of the previous block, creating a chain. A hash is a fixed-length string generated from input data using a mathematical algorithm. Even a tiny change in the input produces a completely different hash.
Input: "Hello World"
Hash: a591a6d40bf420404a011733cfb7b190d62c65bf0bcda32b57b277d9ad9f146e
Input: "Hello World!"
Hash: 7f83b1657ff1fc53b92dc18148a1d65dfc2d4b1fa3d677284addd200126d9069
51% Attack Prevention
To alter the blockchain, an attacker would need to control more than 50% of the network's computing power or stake. This becomes exponentially more difficult and expensive as the network grows. The distributed nature of blockchain makes such attacks impractical for established networks.
Even if an attacker gained majority control, they would need to recalculate all subsequent blocks faster than the honest network, which is computationally infeasible for large blockchains.
Public-Private Key Cryptography
Blockchain uses asymmetric cryptography where each user has a public key (address) and a private key. The public key can be shared freely, while the private key must be kept secret. Transactions are signed with the private key and can be verified using the public key.
Security Warning:Never share your private key with anyone. Anyone with access to your private key has complete control over your assets. There is no password recovery in blockchain systems.
Scalability and Future Developments
While blockchain technology offers numerous advantages, it faces challenges that developers and researchers are actively working to address. Scalability remains one of the primary concerns as blockchain networks grow.
Solutions
Secondary frameworks built on top of existing blockchains to improve transaction speed and reduce costs while maintaining security.
Technology
Dividing the blockchain into smaller pieces (shards) that can process transactions in parallel, significantly increasing throughput.
Protocols
Enabling different blockchains to communicate and share data, creating a more connected blockchain ecosystem.
Modern blockchain platforms like Solana have implemented innovative solutions to address scalability. Solana's combination of Proof of History and Proof of Stake enables it to process thousands of transactions per second, making it suitable for high-performance applications. The Marinade Solana platform leverages these capabilities to provide efficient liquid staking services.
Emerging Trends
- Zero-Knowledge Proofs:Cryptographic methods that allow verification of information without revealing the information itself, enhancing privacy
- Cross-Chain Bridges:Technologies enabling asset transfers between different blockchain networks
- Quantum-Resistant Cryptography:Developing encryption methods that can withstand attacks from quantum computers
- Green Blockchain:Environmentally sustainable consensus mechanisms and carbon-neutral blockchain operations
- Decentralized Autonomous Organizations (DAOs):Blockchain-based governance systems enabling community-driven decision making